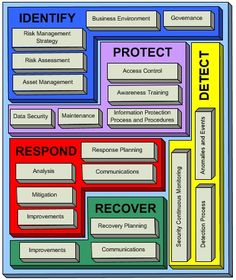
Cyber Security Detection

The importance of system monitoring is echoed in the 10 steps to cyber security guidance provided by the u k.
Cyber security detection. Computer security cybersecurity or information technology security it security is the protection of computer systems and networks from the theft of or damage to their hardware software or electronic data as well as from the disruption or misdirection of the services they provide. Threat detection requires a two pronged approach. The human element includes security analysts who analyze trends patterns in data behaviors and reports as well as those who can determine if anomalous data indicates a potential threat or a false alarm. Our team enables your organization to reduce business risk and improve overall security posture by identifying mitigating and eradicating threats advancing risk management programs.
Until now most companies had a small group of staff responsible for their it and cybersecurity. The field is becoming more important due to increased reliance on computer systems the internet and. For owners and operators of critical infrastructure to mitigate the impacts of cyber attacks and enhance their network security posture. Government s national cyber security centre.
In november of that year the. You need both prevention and detection to respond to cyber incidents. At t managed threat detection and response is built on our own unified security management usm platform which combines the essential security capabilities needed for effective threat detection and response in a single pane of glass key capabilities include asset discovery vulnerability assessment network intrusion detection nids endpoint detection and response edr and siem event. Businesses faced an average of 230 000 cyberattacks according to a recent study.
Preventative security measures such as firewalls secure web gateways and antivirus solutions can no longer defend against sophisticated cyberattacks. Threat detection requires both a human element as well as a technical element. In australia the australian cyber security centre acsc regularly publishes guidance on how organizations can counter the latest cyber security threats. Targeted cyber intrusion detection and mitigation strategies update b targeted cyber intrusion detection and mitigation strategies update b released.
Cybersecurity threat detection julie kittka 2019 09 11t11 18 24 07 00 cyber threats are becoming more of a norm than an exception for businesses in our information driven age.