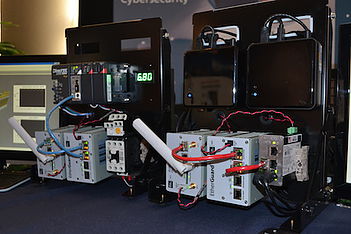
Cyber Security Lab Equipment

17 680 qty item description unit total 25 student workstations w chairs 400 10 000 1 teacher workstation w chair 400 400.
Cyber security lab equipment. The new cyber security lab contains the equipment needed to test the security of industrial control systems and networks from level 1 and 2 controllers and scada systems up to level 4 business networks and out to the internet. Well you are in luck in the build your own cyber lab at home course you will learn how to build a lab from the existing hardware you have. Create a high performance cyber and security testing infrastructure netscout test optimization solutions help you create a high performance cyber and security testing infrastructure that enables instant equipment sharing remote monitoring multiplied dos attack scenarios and topology management via an easy to use software interface. Although most software tools have built in software write blockers you also need an assortment of physical write blockers to cover as many situations or devices as possible.
The equipment specifically used for cybersecurity practices includes. These cyberattacks are usually aimed at accessing changing or destroying sensitive information. The intent of this list is to provide school districts with guidance on the equipment needed to cover the state standards for a cybersecurity program. Cybersecurity is the practice of protecting systems networks and programs from digital attacks.
Also gpgpu based computation is used for augmenting the forensic tasks. By taking this course you will learn a framework to learn new skills technology and software for jobs in either the it or cyber security fields. Advanced cyber forensics lab facilitates research on hardware forensics cloud forensics in memory forensics mobile forensics malware analysis and social media forensics. The school of business telecommunications lab also incorporates a variety of equipment aimed to teach students practical basic and advanced applications of computer networking and cyber security.
Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people and. One 1 rack server composed of ten 10 dell poweredge 860 servers. Or interrupting normal business processes. Equipment and software are purchased.