Cyber Security Problems In Australia

The acsc monitors cyber threats across the globe 24 hours a day seven days a week 365 days a year.
Cyber security problems in australia. The threat of competing countries from years focussed on the dangers of islamist terrorism the western world is. Strategic level policies and programs are struggling to keep up with threats as technology rapidly advances. This enables us to rapidly alert australians to cyber security issues and deliver guidance on what to do in response. A cyber breach can also ruin a company s reputation or customer goodwill.
The cybersecurity environment is a constantly evolving and complex issue that affects numerous sectors. On the government s commitment to increase the cyber. Many businesses are concerned with zero day exploits. In 2017 the average cost of a data breach is 7 35 million.
One example is when the agency discovered that a data breach at a small engineering. Telstra in conjunction with the australian cyber security centre acsc and services australia is boosting australia s cyber resilience through the launch of a new security measure to block malicious text messages. There are many cyber threats that can impact you and your family. The skills shortage in australia s cyber security sector is more severe than initially estimated and is already producing real economic costs.
The threat of nuclear weapons dr davis said australia could be dragged by the alliance with the us into a fight we do. The asd already reaches out to the private sector through its australian cyber security centre acsc of course. However zero day vulnerabilities aren t the problem unpatched known vulnerabilities are the problem. The threat of competing countries 1.
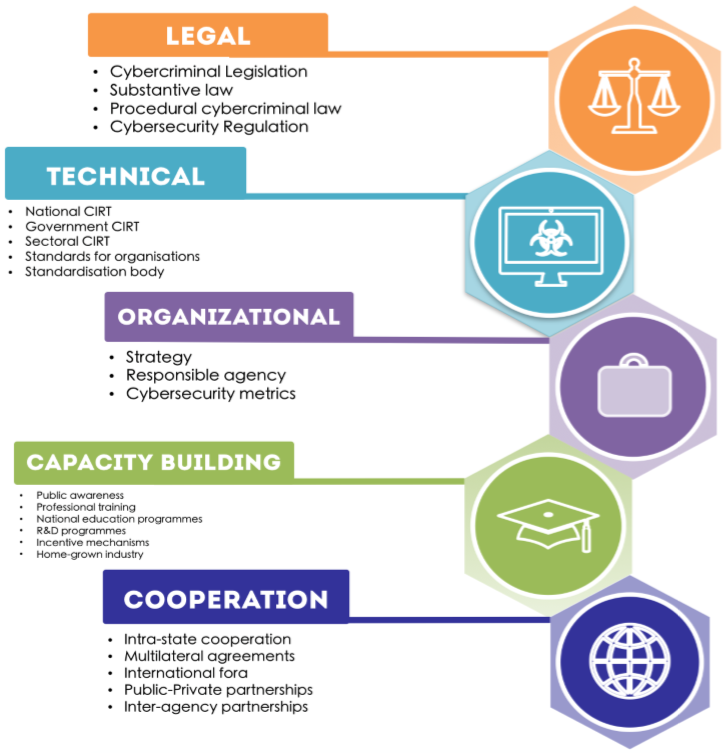
Cyber criminals can access firewalls identification systems and access control to gain access to the network and cause serious damage. While 53 474 reports were received by the australian cybercrime online reporting network. These exploits are those unknown issues with security in programs and systems that have yet to be used against anyone. The problem of cyber crime requires training in cyber security and aggressive controls to protect the data and information.
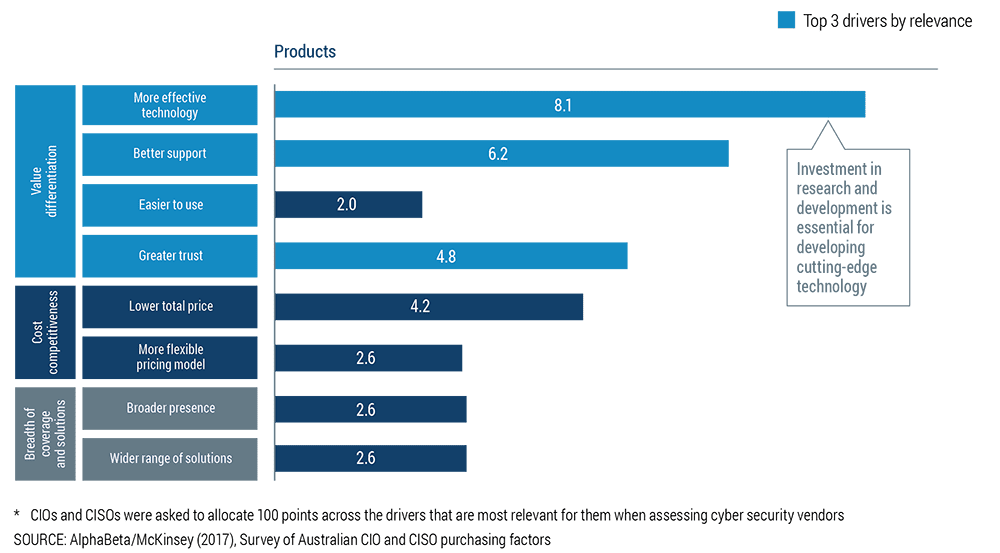
According to the paper au 2 3 billion was stolen by cyber criminals from australian consumers in 2017.