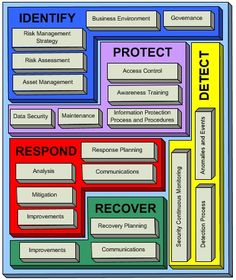
Cyber Security Strategy Uk

It s the most frequently referenced document and project in any cybersecurity discussion.
Cyber security strategy uk. This section shows the list of targeted audiences that the article is written for. The new cyber security strategy sets out how the uk will support economic prosperity protect national security and safeguard the public s way of life by building a more trusted and resilient. Like most major global economies the united kingdom continues to place cybersecurity issues front and center. At the halfway point in delivering the strategy the uk is in a good place in terms of putting in the building blocks necessary to transform the country s cyber security and resilience.
It s also vital that a cyber security strategy is scoped as a business enabler not something that will get in the way of people trying to do their jobs. Protecting and promoting the uk in a digital world our vision is for the uk in 2015 to derive huge economic and social value from a vibrant resilient and secure cyberspace where our actions guided by our core values of liberty fairness transparency and the rule of law enhance prosperity. 2016 2021 document published by the uk government and released nearly two years ago describes the plan to make the uk secure and resilient in cyberspace. But this approach has not achieved the scale and pace of change.
The national cyber security strategy. 8 the uk cyber security strategy. The national cyber security strategy 2016 to 2021 sets out the government s plan to make britain secure and resilient in cyberspace. The national cyber strategy demonstrates my commitment to strengthening america s cybersecurity capabilities and securing america from cyber threats.
It is a call to action for all. It achieved important outcomes by looking to the market to drive secure cyber behaviours.