Cybersecurity Regulations Australia

Cybersecurity laws and regulations 2020.
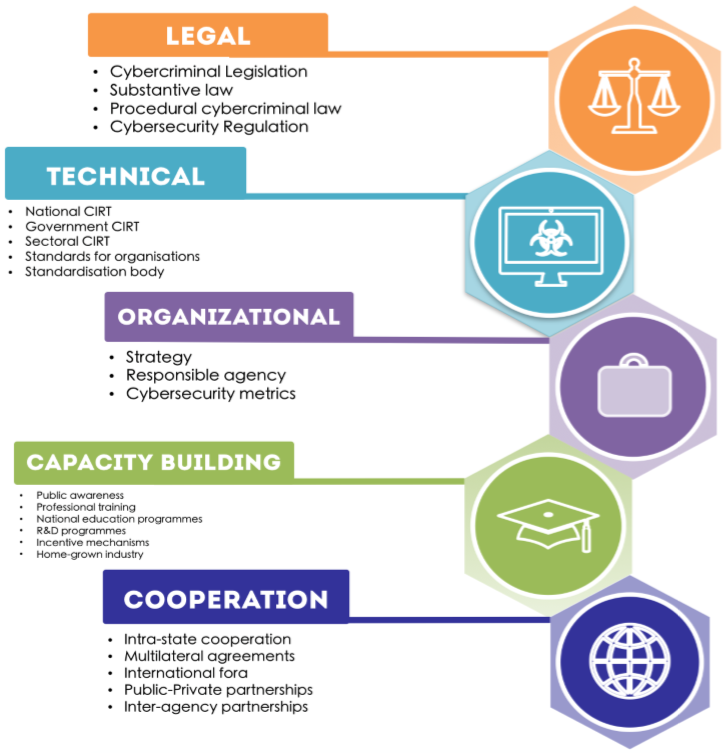
Cybersecurity regulations australia. The australian signals directorate asd is the commonwealth s peak advisory body on cyber security. A structured guide to cybersecurity in australia. Its 2012 publication top four mitigation strategies to protect your ict system sets out four cyber security strategies which it says if implemented can address up to 85 of targeted cyber intrusions. Resolving this challenge is a key goal of the standards australia task force whose work will not only develop clear cybersecurity guidance but will inform the ongoing development of the government s 2020 cyber security strategy which has received over 210 submissions as part of what department of home affairs guidance calls an ongoing.
Iso iec 27001 iso 27002 1 2. Our role is to help make australia the safest place to connect online. However that doesn t mean all businesses don t need to comply with cybersecurity standards. The cybersecurity standards set to impact every australian business and director.
The top cybersecurity frameworks are as discussed below. Businesses should understand cybersecurity frameworks for enhancing organizational security. That s because some kinds of establishments that offer specific services have applicable regulations. The acsc s cyber security mission is supported by asd s wider organisation whose role is to provide foreign signals intelligence and has a long history of cyber security excellence.
It may be surprising that an overarching federal cybersecurity law doesn t yet exist in the united states. Standards australia has a critical cyber security capacity building role within the pacific region as part of the australian government s cyber engagement strategy. The iso 27001 cybersecurity framework consists of international standards which recommend the requirements for managing information security management systems isms. Iclg cybersecurity laws and regulations australia covers common issues in cybersecurity laws and regulations including criminal activity applicable laws specific sectors corporate governance litigation insurance employees and investigatory and police powers in 32 jurisdictions.
Currently the regulatory framework for cybersecurity in australia is haphazard with no mandatory best practice minimum security standards for businesses and the implications for a cyber attack potentially extending to multiple breaches of corporations privacy and criminal laws as well as industry specific financial energy health and. The program began in august 2018 with the final report being released at the beginning of 2020.